|
|
2 years ago | |
|---|---|---|
| .github/workflows | 3 years ago | |
| addon | 3 years ago | |
| assets | 4 years ago | |
| cert | 3 years ago | |
| cmd | 2 years ago | |
| examples | 3 years ago | |
| proxy | 2 years ago | |
| web | 2 years ago | |
| .gitignore | 3 years ago | |
| .goreleaser.yml | 2 years ago | |
| LICENSE | 5 years ago | |
| Makefile | 2 years ago | |
| README.md | 2 years ago | |
| README_CN.md | 2 years ago | |
| go.mod | 2 years ago | |
| go.sum | 2 years ago | |
README.md
go-mitmproxy
go-mitmproxy is a Golang implementation of mitmproxy that supports man-in-the-middle attacks and parsing, monitoring, and tampering with HTTP/HTTPS traffic.
Key features
- Parses HTTP/HTTPS traffic and displays traffic details via a web interface.
- Supports a plugin mechanism for easily extending functionality. Various event hooks can be found in the examples directory.
- HTTPS certificate handling is compatible with mitmproxy and stored in the
~/.mitmproxyfolder. If the root certificate is already trusted from a previous use ofmitmproxy,go-mitmproxycan use it directly. - Refer to the configuration documentation for more features.
Unsupported features
- Only supports setting the proxy manually in the client, not transparent proxy mode.
- Currently does not support HTTP/2 protocol parsing or WebSocket protocol parsing.
For more information on the difference between manually setting a proxy and transparent proxy mode, please refer to the mitmproxy documentation for the Python version: How mitmproxy works. go-mitmproxy currently supports "Explicit HTTP" and "Explicit HTTPS" as mentioned in the article.
Command Line Tool
Installation
go install github.com/lqqyt2423/go-mitmproxy/cmd/go-mitmproxy@latest
Usage
Use the following command to start the go-mitmproxy proxy server:
go-mitmproxy
After starting, the HTTP proxy address is set to port 9080 by default, and the web interface is set to port 9081 by default.
The certificate needs to be installed after the first startup to parse HTTPS traffic. The certificate will be automatically generated after the first startup command and stored in ~/.mitmproxy/mitmproxy-ca-cert.pem. Installation steps can be found in the Python mitmproxy documentation: About Certificates.
Additional Parameters
ou can use the following command to view more parameters of go-mitmproxy:
go-mitmproxy -h
Usage of go-mitmproxy:
-addr string
proxy listen addr (default ":9080")
-allow_hosts value
a list of allow hosts
-cert_path string
path of generate cert files
-debug int
debug mode: 1 - print debug log, 2 - show debug from
-f string
Read configuration from file by passing in the file path of a JSON configuration file.
-ignore_hosts value
a list of ignore hosts
-ssl_insecure
not verify upstream server SSL/TLS certificates.
-version
show go-mitmproxy version
-web_addr string
web interface listen addr (default ":9081")
Importing as a package for developing functionalities
Simple Example
package main
import (
"log"
"github.com/lqqyt2423/go-mitmproxy/proxy"
)
func main() {
opts := &proxy.Options{
Addr: ":9080",
StreamLargeBodies: 1024 * 1024 * 5,
}
p, err := proxy.NewProxy(opts)
if err != nil {
log.Fatal(err)
}
log.Fatal(p.Start())
}
Adding Functionality by Developing Plugins
Refer to the examples for adding your own plugins by implementing the AddAddon method.
The following are the currently supported event nodes:
type Addon interface {
// A client has connected to mitmproxy. Note that a connection can correspond to multiple HTTP requests.
ClientConnected(*ClientConn)
// A client connection has been closed (either by us or the client).
ClientDisconnected(*ClientConn)
// Mitmproxy has connected to a server.
ServerConnected(*ConnContext)
// A server connection has been closed (either by us or the server).
ServerDisconnected(*ConnContext)
// The TLS handshake with the server has been completed successfully.
TlsEstablishedServer(*ConnContext)
// HTTP request headers were successfully read. At this point, the body is empty.
Requestheaders(*Flow)
// The full HTTP request has been read.
Request(*Flow)
// HTTP response headers were successfully read. At this point, the body is empty.
Responseheaders(*Flow)
// The full HTTP response has been read.
Response(*Flow)
// Stream request body modifier
StreamRequestModifier(*Flow, io.Reader) io.Reader
// Stream response body modifier
StreamResponseModifier(*Flow, io.Reader) io.Reader
}
WEB Interface
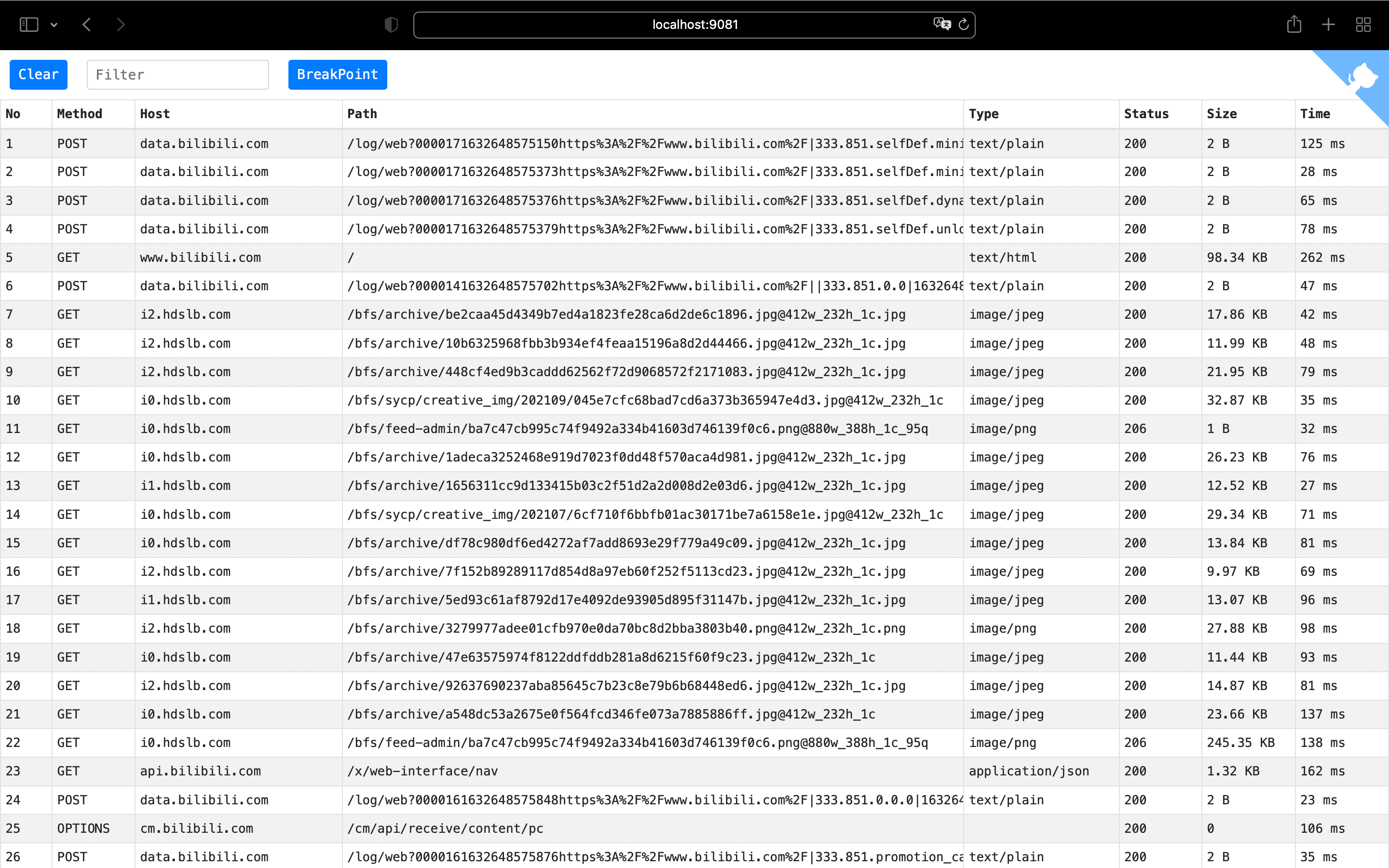
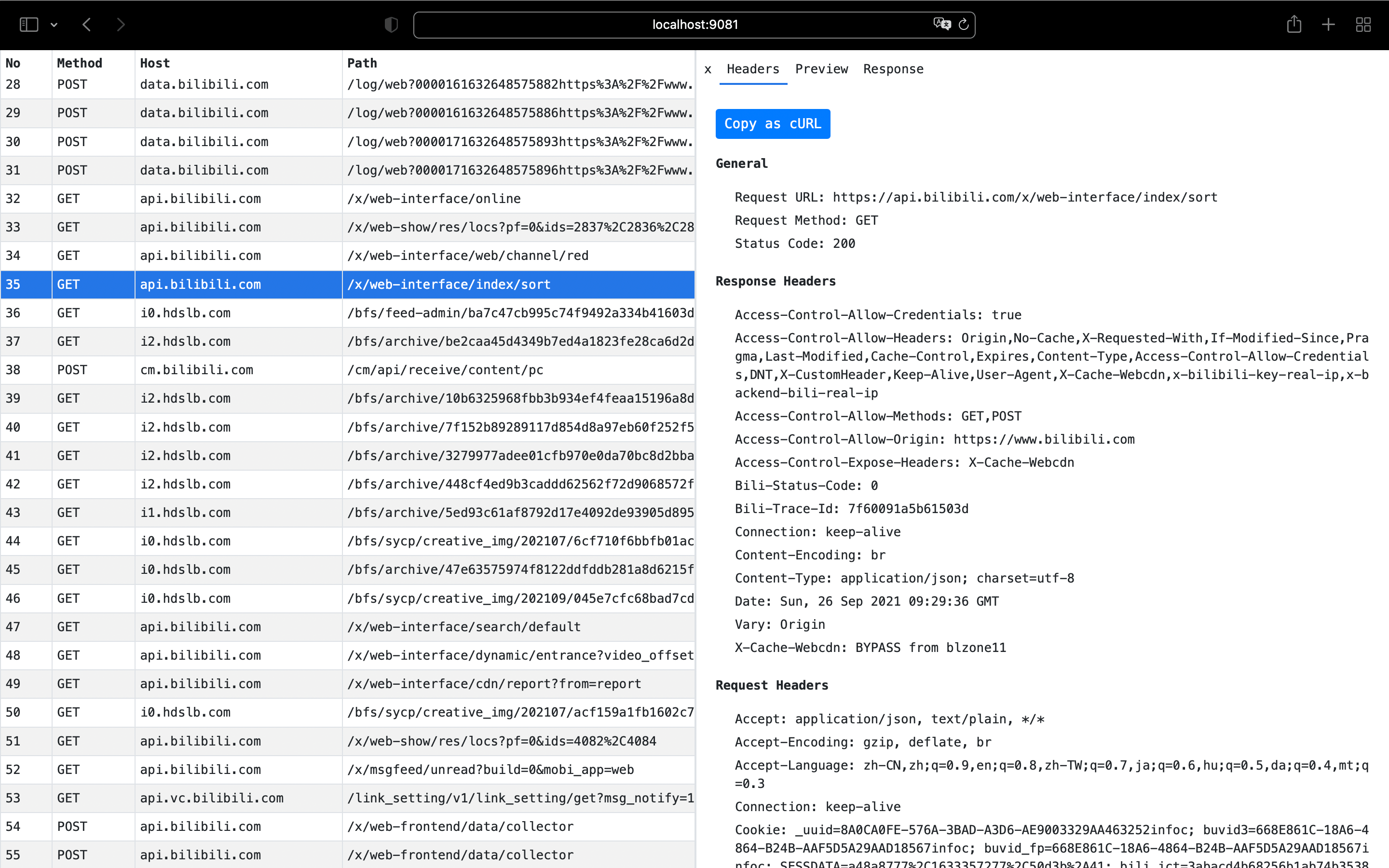
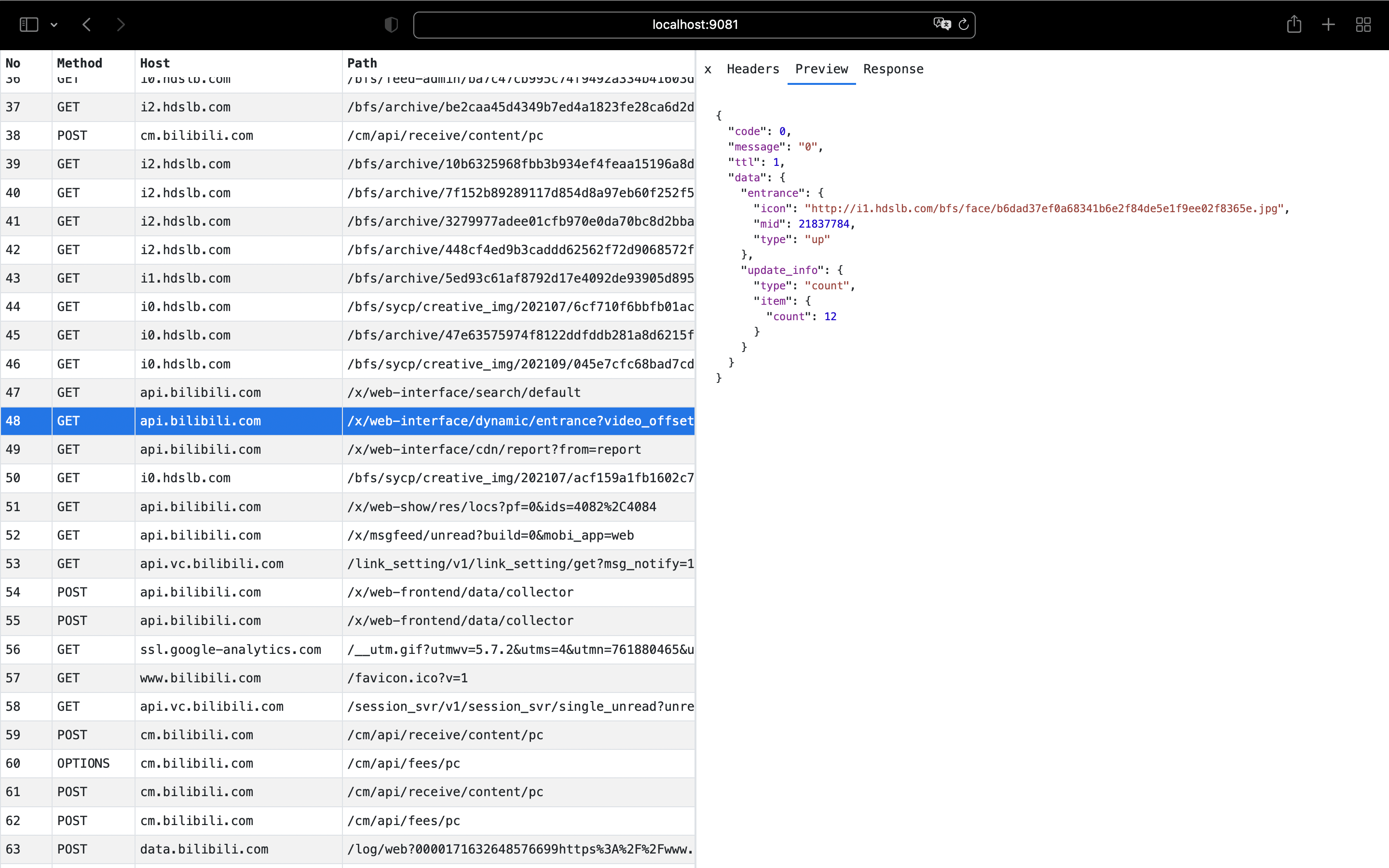
You can access the web interface at http://localhost:9081/ using a web browser.
Features
- View detailed information of HTTP/HTTPS requests
- Supports formatted preview of JSON requests/responses
- Supports binary mode to view response body
- Supports advanced filtering rules
- Supports request breakpoint function